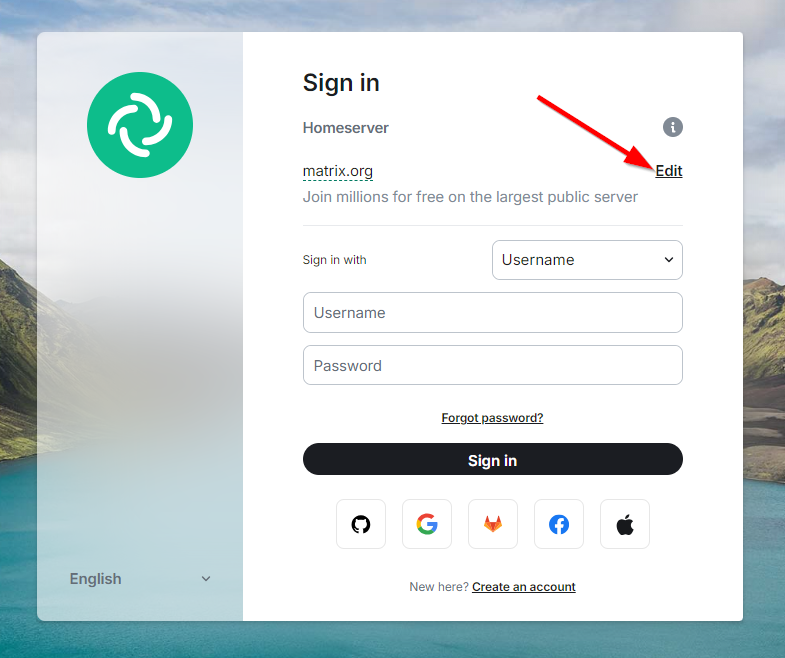
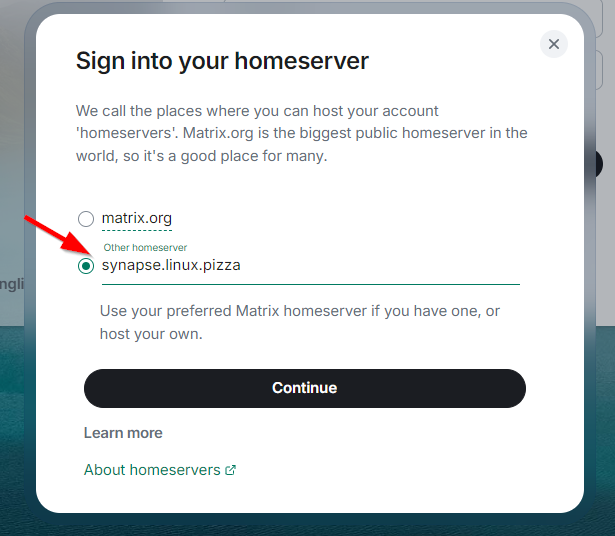
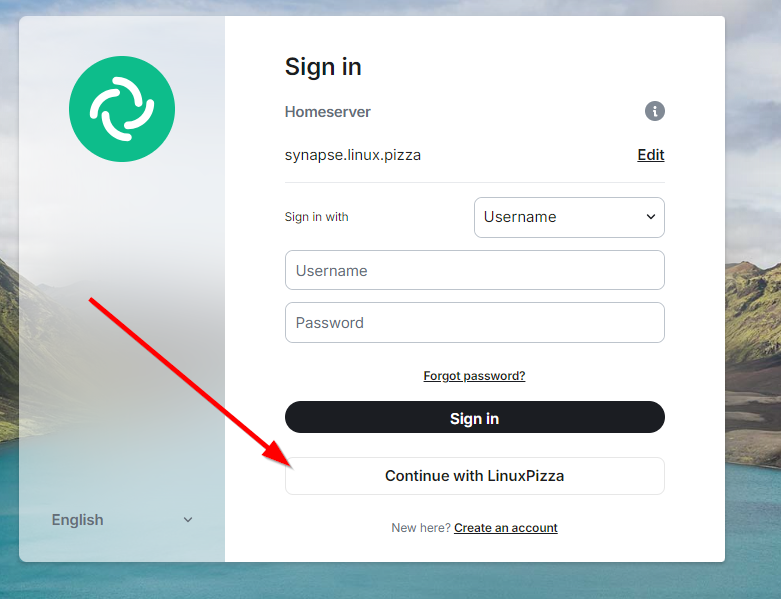
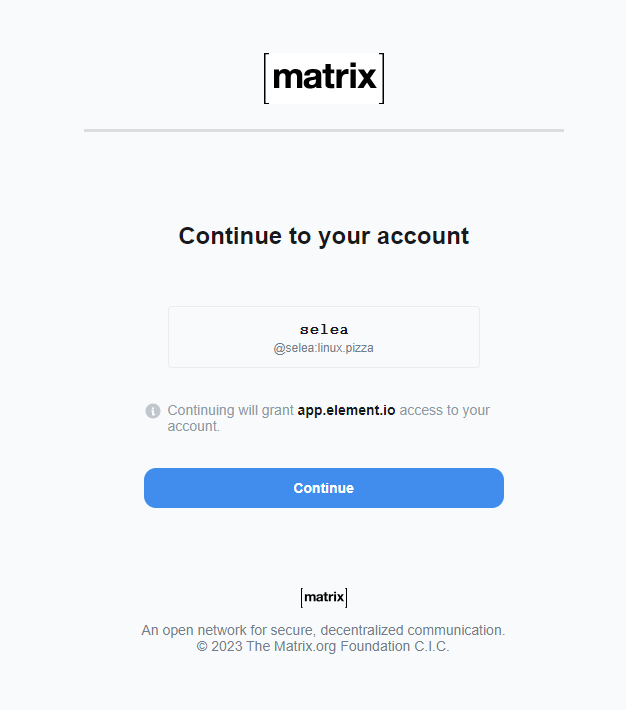
LVM stuff
WARNING: PV /dev/sda2 in VG vg0 is using an old PV header, modify the VG to update.
Update the metadata with the vgck command – where the “vg0” is your own pool.
vgck --updatemetadata vg0
curl stuff
Curl a specific IP with a another host-header
curl -H "Host: subdomain.example.com" http://172.243.6.400/
git stuff
tell git.exe to use the built-in CA-store in Windows
git config --global http.sslBackend schannel
random stuff
See which process is using a file
fuser file
Import RootCert into Java-keystore example
sudo /usr/lib/java/jdk8u292-b10-jre/bin/keytool -import -alias some-rootcert -keystore /usr/lib/java/jdk8u292-b10-jre/lib/security/cacerts -file /usr/share/ca-certificates/extra/someRoot.crt`
Apache2 configs example
Enable AD-authentication for web-resources
<Location />
AuthName "AD authentication"
AuthBasicProvider ldap
AuthType Basic
AuthLDAPGroupAttribute member
AuthLDAPGroupAttributeIsDN On
AuthLDAPURL ldap://IP:389/OU=Users,OU=pizza,DC=linux,DC=pizza?
sAMAccountName?sub?(objectClass=*)
AuthLDAPBindDN cn=tomcat7,ou=ServiceAccounts,ou=Users,OU=pizza,dc=linux,dc=pizza
AuthLDAPBindPassword "exec:/bin/cat /etc/apache2/ldap-password.conf"
Require ldap-group
CN=some_group,OU=Groups,OU=pizza,DC=linux,DC=pizza
ProxyPass "http://localhost:5601/"
ProxyPassReverse "http://localhost:5601/"
</Location>
Insert Matomo tracking script in Apache using mod_substitute
AddOutputFilterByType SUBSTITUTE text/html
Substitute "s-</head>-<script type=\"text/javascript\">var _paq = _paq || [];_paq.push(['trackPageView']);_paq.push(['enableLinkTracking']);(function() {var u=\"https://matomo.example.com/\";_paq.push(['setTrackerUrl', u+'matomo.php']);_paq.push(['setSiteId', '1']);var d=document, g=d.createElement('script'), s=d.getElementsByTagName('script')[0];g.type='text/javascript'; g.async=true; g.defer=true; g.src=u+'matomo.js'; s.parentNode.insertBefore(g,s);})();</script></head>-n"
Load balance backend-servers
<Proxy balancer://k3singress>
BalancerMember http://x.x.x.1:80
BalancerMember http://x.x.x.2:80
BalancerMember http://x.x.x.3:80
BalancerMember http://x.x.x.4:80
ProxySet lbmethod=bytraffic
ProxySet connectiontimeout=5 timeout=30
SetEnv force-proxy-request-1.0 1
SetEnv proxy-nokeepalive 1
</Proxy>
ProxyPass "/" "balancer://k3singress/"
ProxyPassReverse "/" "balancer://k3singress/"
ProxyVia Full
ProxyRequests On
ProxyPreserveHost On
Basic Apache-config for PHP-FPM
<VirtualHost *:80>
ServerName www.example.com
DocumentRoot /srv/www.example.com/htdocs
<Directory /srv/www.example.com/htdocs>
AllowOverride All
Require all granted
DirectoryIndex index.html index.htm index.php
<FilesMatch "\.php$">
SetHandler proxy:unix:/run/php/www.example.com.sock|fcgi://localhost
</FilesMatch>
</Directory>
SetEnvIf x-forwarded-proto https HTTPS=on
</VirtualHost>
Basic PHP-fpm pool
[www.example.com]
user = USER
group = GROUP
listen = /var/run/php/$pool.sock
listen.owner = www-data
listen.group = www-data
pm = ondemand
pm.process_idle_timeout = 10
pm.max_children = 1
chdir = /
php_admin_value[sendmail_path] = /usr/sbin/sendmail -t -i -f no-reply@ftp.selea.se
php_admin_value[mail.log] = /srv/ftp.selea.se/log/mail.log
php_admin_value[open_basedir] = /srv/ftp.selea.se:/tmp
php_admin_value[memory_limit] = 64M
php_admin_value[upload_max_filesize] = 64M
php_admin_value[post_max_size] = 64M
php_admin_value[max_execution_time] = 180
php_admin_value[max_input_vars] = 1000
php_admin_value[disable_functions] = passthru,exec,shell_exec,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source,mail
Netplan – use device MAC instead of /etc/machine-id for DHCP
network:
ethernets:
eth0:
dhcp4: true
dhcp-identifier: mac
version: 2
HPs apt repo for various utilities for proliant machines
deb http://downloads.linux.hpe.com/SDR/repo/mcp buster/current non-free
psql stuff
CREATE DATABASE yourdbname;
CREATE USER youruser WITH ENCRYPTED PASSWORD 'yourpass';
GRANT ALL PRIVILEGES ON DATABASE yourdbname TO youruser;
Get entity for AD/SMB based user so you can put it in /etc/passwd:
getent passwd USERNAME
Nicely shutdown NetApp cluster
system node autosupport invoke -node * -type all -message "MAINT=48h Power Maintenance"
system node halt -node * -skip-lif-migration-before-shutdown true -ignore-quorum-warnings true -inhibit-takeover true
Allow a process to listen on ports 0-1000 in systemd.service file
[Service]
AmbientCapabilities=CAP_NET_BIND_SERVICE
#linux #kubernetes #netplan #php-fpm #apache #LVM